This guide provides an overview of the different sections of the Cylance console and provides you with links to the Cylance Endpoint Security docs for more information.
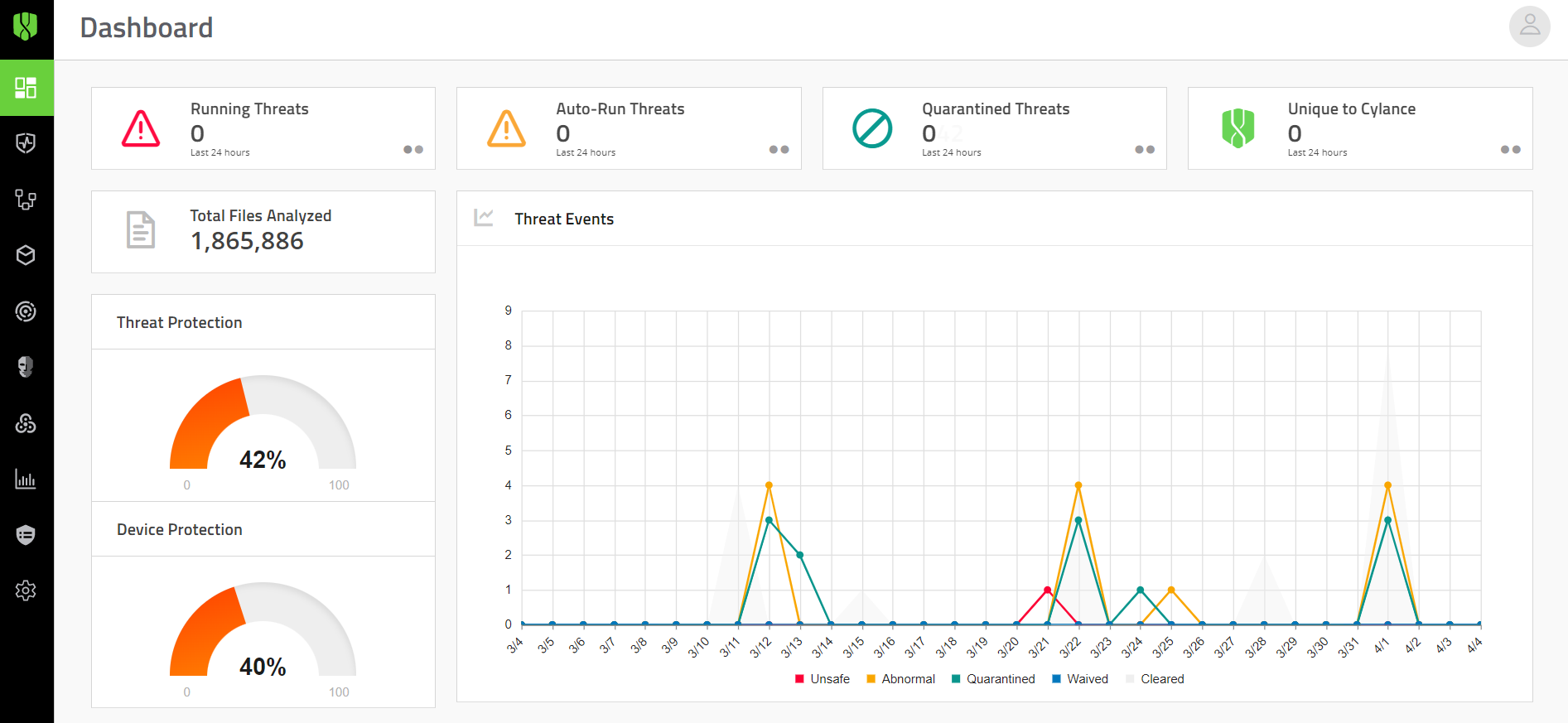
The management console dashboards offer helpful visualizations and statistical summaries of the data collected and analyzed by different Cylance Endpoint Security services.
See Using dashboards.
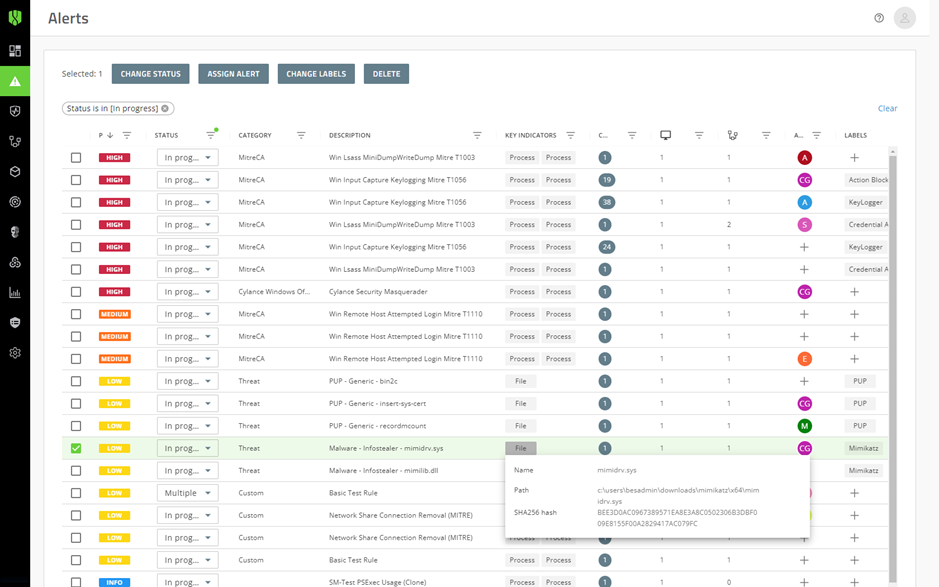
The Alerts view gives you a comprehensive way to review the alerts that are detected and correlated across Cylance Endpoint Security services, making it easier for you to identify and track prevailing threat patterns and resolve groups of alerts efficiently.
See Managing alerts across Cylance Endpoint Security services.
You can use the screens available in this section to review and respond to threats detected by CylancePROTECT Desktop and CylancePROTECT Mobile.
You can use zones to group and manage CylancePROTECT Desktop and CylanceOPTICS devices. Zones are the most efficient way to manage the application of device policies to groups of devices.
See Setting up zones.
Use the Assets screens to view and manage the devices and users that are actively using Cylance Endpoint Security services and features.
Use this section of the console to review and explore the forensic data collected from CylanceOPTICS devices and to take action in response to threats.
See Analyzing data collected by CylanceOPTICS and Using CylanceOPTICS to detect and respond to events.
Use this section to review and investigate the events and files detected by CylanceAVERT.
Use the CylanceGATEWAY screen to monitor the events detected by the CylanceGATEWAY agent on desktop devices and the CylancePROTECT Mobile app on mobile devices. Events are reported only if Work Mode or Safe Mode is enabled.
Use this screen to generate and review reports about CylancePROTECT Desktop devices and threats.
Use this section of the management console to configure and assign policies that define the behavior of Cylance Endpoint Security features and services.
Use this section of the management console to configure various settings to customize Cylance Endpoint Security services and features to meet your organization’s needs.
See the Cylance Endpoint Security docs for complete product information and help resources, including:
- Release Notes: Fixed and known issues and information about what’s new for each Cylance Endpoint Security service.
- Overview and Architecture Guide: A comprehensive overview of services and features, including architecture diagrams and select data flows.
- Setup: Instructions for setting up your Cylance Endpoint Security environment and services.
- Administration: Instructions for the day-to-day management of services and features.
- User Guides: Instructions for end users of the CylancePROTECT Mobile app and desktop agents.
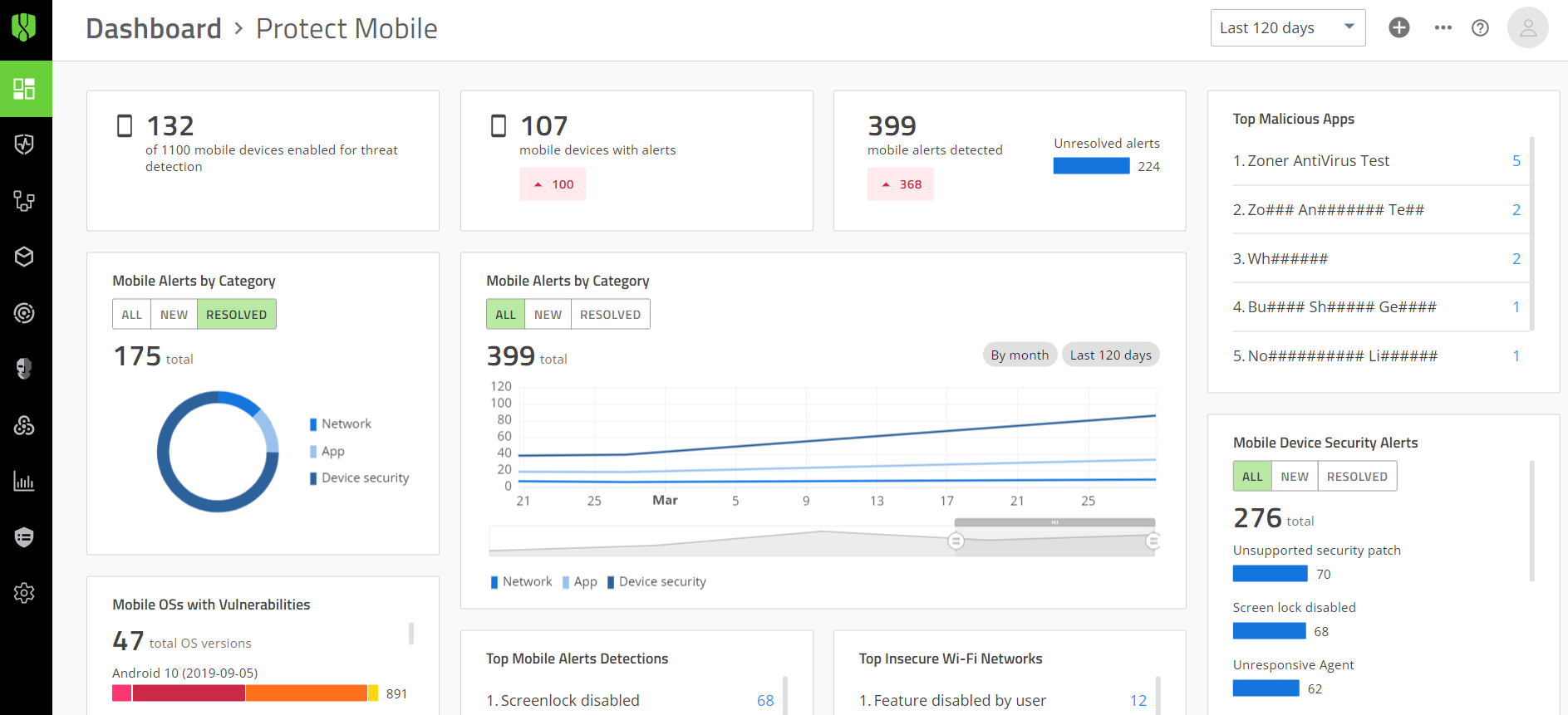
Screens to manage CylancePROTECT Desktop
Screens to manage CylancePROTECT Mobile
- Protect Mobile Alerts
- Vulnerabilities: A list of the common vulnerabilities and exposures (as identified, defined, and tracked by the National Vulnerability Database) for each device OS that the CylancePROTECT Mobile app is installed on.
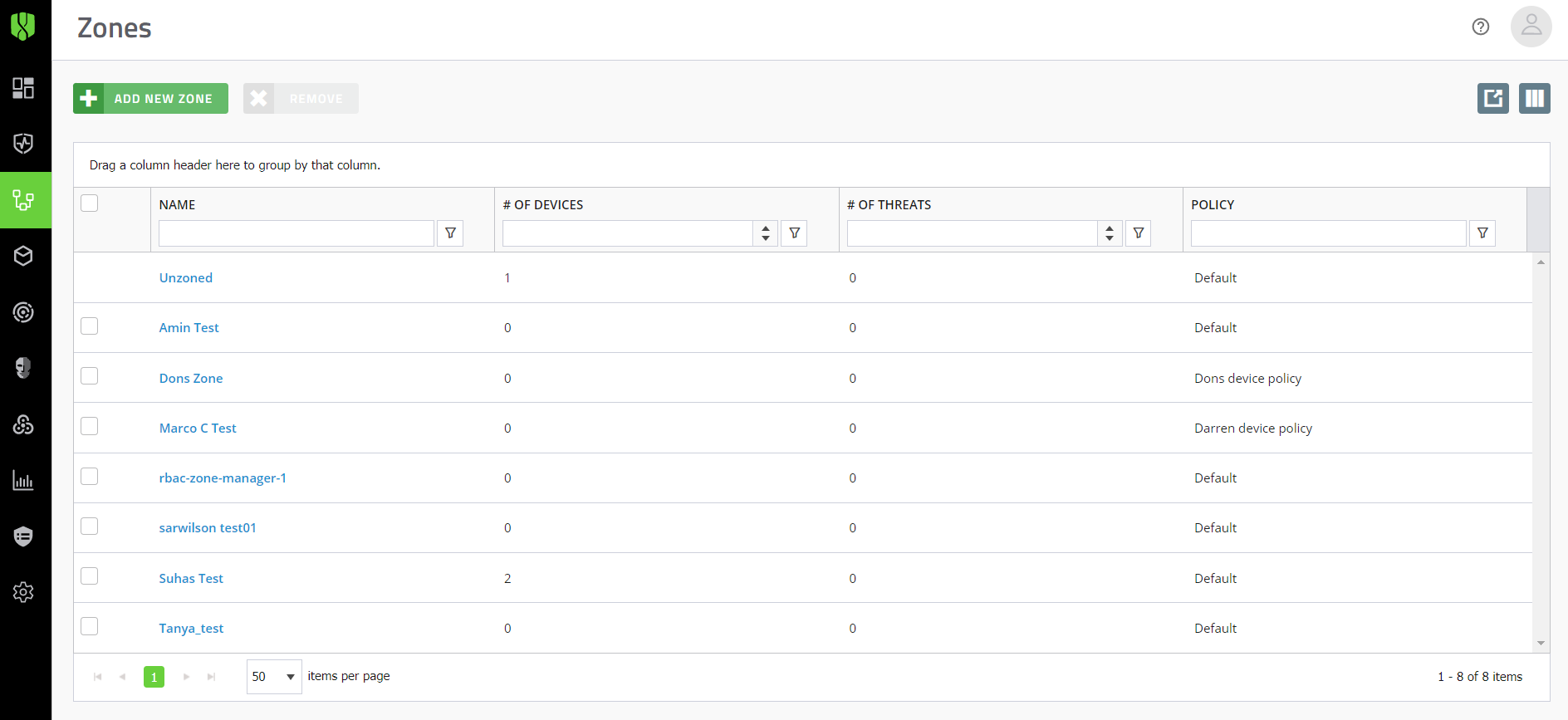
You can also use zones to easily manage updates of the CylancePROTECT and CylanceOPTICS agents on devices.
See Managing updates for the CylancePROTECT Desktop and CylanceOPTICS agents.
Devices
Applies to: CylancePROTECT Desktop, CylanceOPTICS
- Download agent installers
- View device details
- Assign device policies
- Add devices to zones
- Remove devices
- Device lifecycle management
See Manage CylancePROTECT Desktop and CylanceOPTICS devices.
Mobile Devices
Applies to: CylancePROTECT Mobile, CylanceGATEWAY (mobile only)
- View alerts
- View a device’s current risk level
- View compliance details
See Manage devices with the CylancePROTECT Mobile app.
Unprotected Devices
Applies to: CylancePROTECT Desktop
- View devices discovered from Active Directory that are not protected by CylancePROTECT Desktop
See Discover unprotected devices.
Avert Users
Applies to: CylanceAVERT
- View user information and details
- View device details
- Manage users
- View Avert events
- Assign user groups
- Assign user policies
See Managing CylanceAVERT users.
Users
Applies to: CylancePROTECT Mobile, CylanceGATEWAY (mobile and desktop)
- View alerts and events
- View device details
- Manage group membership
- Assign user policies
- Send activation emails for the CylancePROTECT Mobile app
See Manage CylancePROTECT Mobile and Gateway users.
User Groups
Applies to: CylancePROTECT Mobile, CylanceGATEWAY (mobile and desktop)
- Manage group membership
- Assign user policies to groups
See Manage user groups.
Installed Applications
Applies to: CylancePROTECT Desktop
- View installed software applications
See View a list of applications installed on CylancePROTECT Desktop devices
Detections
View and analyze the events detected by the CylanceOPTICS agent. Use the detections dashboard to review trends over time, the severity of different detections, and detailed information about each detection. See View and manage detections.
InstaQuery
Construct queries to analyze artifact data, discover indicators of compromise, and to determine the prevalence of artifacts on devices. See Using InstaQuery and advanced query to analyze artifact data.
Advanced Query
Construct your own queries with EQL syntax for advanced threat-hunting. See Using InstaQuery and advanced query to analyze artifact data.
Focus Data
Request focus data to visualize and analyze the chain of events, and the associated artifacts and facets of those events, that resulted in a piece of malware or other security threats on a device. See View focus data.
Packages
Deploy custom or preconfigured packages to collect data from devices for further analysis. For example, you can run a process to collect browser data. See Deploy a package to collect data from devices.
Devices
View details and status information for all CylanceOPTICS devices. See View devices that are enabled for CylanceOPTICS.
Action History
Retrieve and review remote response logs and download files that CylanceOPTICS has identified as potential threats. See View and download files that CylanceOPTICS has retrieved.
Configurations
Configure detection rule sets and exceptions, create custom detection rules, and create packages and package playbooks. See Using CylanceOPTICS to detect and respond to events.
Events
View the events detected by the CylanceAVERT agent. Click an event to view details in the event details drawer. See CylanceAVERT events.
File Inventory
View the potentially sensitive files detected by the CylanceAVERT agent. See View the file inventory to identify sensitive files.
Partially Analyzed Files
View the files that were only partially scored by CylanceAVERT for sensitive information. See View partially analyzed files.
Evidence Locker
View details and download files that were involved in a data exfiltration event. See Use the evidence locker to view exfiltration event details.
CylancePROTECT Desktop and CylanceOPTICS
Also see Enable and configure CylanceOPTICS.
CylancePROTECT Mobile
User policies:
CylanceGATEWAY
User policies:
CylanceAVERT
User policies:
Application
- View, delete, or regenerate the installation token for the CylancePROTECT Desktop agent.
- View, disable, or generate an invitation URL for CylancePROTECT Desktop users.
- Configure whether users must provide a password to remove the CylancePROTECT Desktop agent and CylanceOPTICS agent.
- Configure Cylance Endpoint Security to send events for different services and features to a SIEM solution or syslog server. See Send events to a SIEM solution or syslog server.
- Configure custom authentication for the management console. See Custom authentication.
- Access detailed CylancePROTECT Desktop threat data reports. See Using CylancePROTECT Desktop reports.
Administrators
Assign administrator roles to users and create your own roles with custom permissions. Roles and their associated permissions control the features that an administrator can view and modify throughout the console.
See Setting up administrators.
Global List
Add files to the global quarantine or safe list to control whether they are blocked or permitted on CylancePROTECT Desktop devices.
See Add a file to the CylancePROTECT Desktop global quarantine or global safe list.
Global List (Mobile)
You can use the safe list to exempt a specific app or developer signing certificate from CylancePROTECT Mobile malware and sideload detection, or an IP address or domain from CylancePROTECT Mobile message scanning. You can use the restricted list to classify a specific app, developer signing certificate, IP address, or domain as a threat as soon as it is detected by these features.
See Add an app, certificate, IP address, or domain to a CylancePROTECT Mobile safe or restricted list.
Detection and Response
Create custom partial lockdown configurations for CylanceOPTICS devices.
See Lock a device.
Deployments
Download the installers for the CylancePROTECT Desktop and CylanceOPTICS agents.
Update
Manage updates of the CylancePROTECT Desktop and CylanceOPTICS agents.
See Managing updates for the Cylance Endpoint Security agents.
Certificates
Add a certificate to the certificates safe list to allow the associated software to run without interruption on CylancePROTECT Desktop devices.
See Add a certificate to the CylancePROTECT Desktop global safe list.
Integrations
Integrate Cylance Endpoint Security with third-party programs using the BlackBerry User API.
See Enable access to the Cylance User API.
Device Lifecycle
Configure the time period before an offline CylancePROTECT Desktop device is considered inactive.
See Configure device lifecycle management.
Authentication
Add an authenticator so that you can use an identity store like Active Directory or myAccount, or an identity or multi-factor authentication provider like Okta, Ping Identity, or Duo, to specify the types of authentication users must complete to access the management console or to activate the CylancePROTECT Mobile app or the CylanceGATEWAY agent.
See Add an authenticator.
Directory Connections
Connect Cylance Endpoint Security to your organization’s directory to onboard users for the CylancePROTECT Mobile and CylanceGATEWAY services.
See Installing the BlackBerry Connectivity Node and Linking to your company directory.
Connectors
Connect Cylance Endpoint Security to EMM solutions such as Microsoft Intune to enable the reporting of device risk levels to the EMM solution. The device risk level is calculated based on the detection of mobile threats by the CylancePROTECT Mobile app on devices. The EMM solution can execute mitigation actions based on the device risk level.
See Integrating Cylance Endpoint Security with Intune to respond to mobile threats.
Network
Configure settings to customize the features and functionality of CylanceGATEWAY.
See Setting up CylanceGATEWAY.
Information Protection
Configure settings to customize the features and functionality of CylanceAVERT.
See Define sensitive content using information protection settings.
Activation
Configure how long activation credentials are valid for the CylancePROTECT Mobile app and the CylanceGATEWAY agent.
See Enrolling CylancePROTECT Mobile and CylanceGATEWAY users.