- Configuring BlackBerry UEM for the first time
- Changing BlackBerry UEM certificates
- Configuring BlackBerry UEM to send data through a proxy server
- Configuring connections through internal proxy servers
- Connecting to your company directories
- Configuring Microsoft Active Directory authentication in an environment that includes Exchange linked mailboxes
- Connect to a Microsoft Active Directory instance
- Connect to an LDAP directory
- Enable directory-linked groups
- Enabling onboarding
- Synchronize a company directory connection
- Removing a connection to a company directory
- Connecting to an SMTP server to send email notifications
- Configuring database mirroring
- Connecting BlackBerry UEM to Microsoft Azure
- Create a Microsoft Azure account
- Synchronize Microsoft Active Directory with Microsoft Azure
- Create an app registration in Azure
- Configuring Azure Active Directory conditional access
- Configure BlackBerry UEM as a Compliance Partner in Azure
- Configure Azure Active Directory conditional access
- Configure the BlackBerry Dynamics connectivity profile to support the Azure Conditional Access feature
- Assign the Feature - Azure conditional access app to users
- Configure a BlackBerry Dynamics Profile
- Remove devices from Azure Active Directory conditional access
- Enable access to the BlackBerry Web Services over the BlackBerry Infrastructure
- Obtaining an APNs certificate to manage iOS and macOS devices
- Configuring BlackBerry UEM for DEP
- Configuring BlackBerry UEM to support Android Enterprise devices
- Extending the management of Chrome OS devices to BlackBerry UEM
- Setting up management of Chrome OS devices if you have already configured BlackBerry UEM to use Android Enterprise
- Create a service account that BlackBerry UEM uses to authenticate with your Google Cloud or Google Workspace by Google domain
- Enable additional APIs to allow BlackBerry UEM to sync the Chrome OS data
- Integrate BlackBerry UEM with your Google Cloud or Google Workspace by Google domain so you can use Chrome OS devices
- Synchronize BlackBerry UEM with the Google admin console
- Simplifying Windows 10 activations
- Migrating users, devices, groups, and other data from a source server
- Prerequisites: Migrating users, devices, groups, and other data from a source server
- Connect to a source server
- Considerations: Migrating IT policies, profiles, and groups from a source server
- Migrate IT policies, profiles, and groups from a source server
- Complete policy and profile migration for BlackBerry Dynamics-activated users
- Considerations: Migrating users from a source server
- Migrate users from a source server
- Considerations: Migrating devices from a source server
- Migrate devices from a source server
- Migrating DEP devices
- Configuring BlackBerry UEM to support BlackBerry Dynamics apps
- Manage BlackBerry Proxy clusters
- Configure Direct Connect using port forwarding
- Configure BlackBerry Dynamics properties
- Configure communication settings for BlackBerry Dynamics apps
- Sending BlackBerry Dynamics app data through an HTTP proxy
- BlackBerry Dynamics connectivity and routing behavior
- Default routing
- Example routing scenarios
- Scenario 1: Route traffic to specific servers or domains through BlackBerry Proxy
- Scenario 2: Route all traffic through the BlackBerry Proxy and then through a web proxy server
- Scenario 3: Route some traffic internally for most apps but configure a proxy server specifically for web browsing using BlackBerry Access
- BlackBerry Dynamics data flow
- Configuring Kerberos for BlackBerry Dynamics apps
- Connect BlackBerry UEM to a BlackBerry Dynamics PKI connector
- Integrating BlackBerry UEM with Cisco ISE
- Requirements: Integrating BlackBerry UEM with Cisco ISE
- Create an administrator account that Cisco ISE can use
- Add the BlackBerry Web Services certificate to the Cisco ISE certificate store
- Connect BlackBerry UEM to Cisco ISE
- Example: Authorization policy rules for BlackBerry UEM
- Managing network access and device controls using Cisco ISE
- BlackBerry Docs
- BlackBerry UEM 12.17
- Installation and configuration
- Configuration
- Configuring BlackBerry UEM to support BlackBerry Dynamics apps
- Configuring Kerberos for BlackBerry Dynamics apps
- Domains, realms, and forests
- Multi-realm Kerberos environment, single-forest configuration
Multi-realm Kerberos environment, single-forest configuration
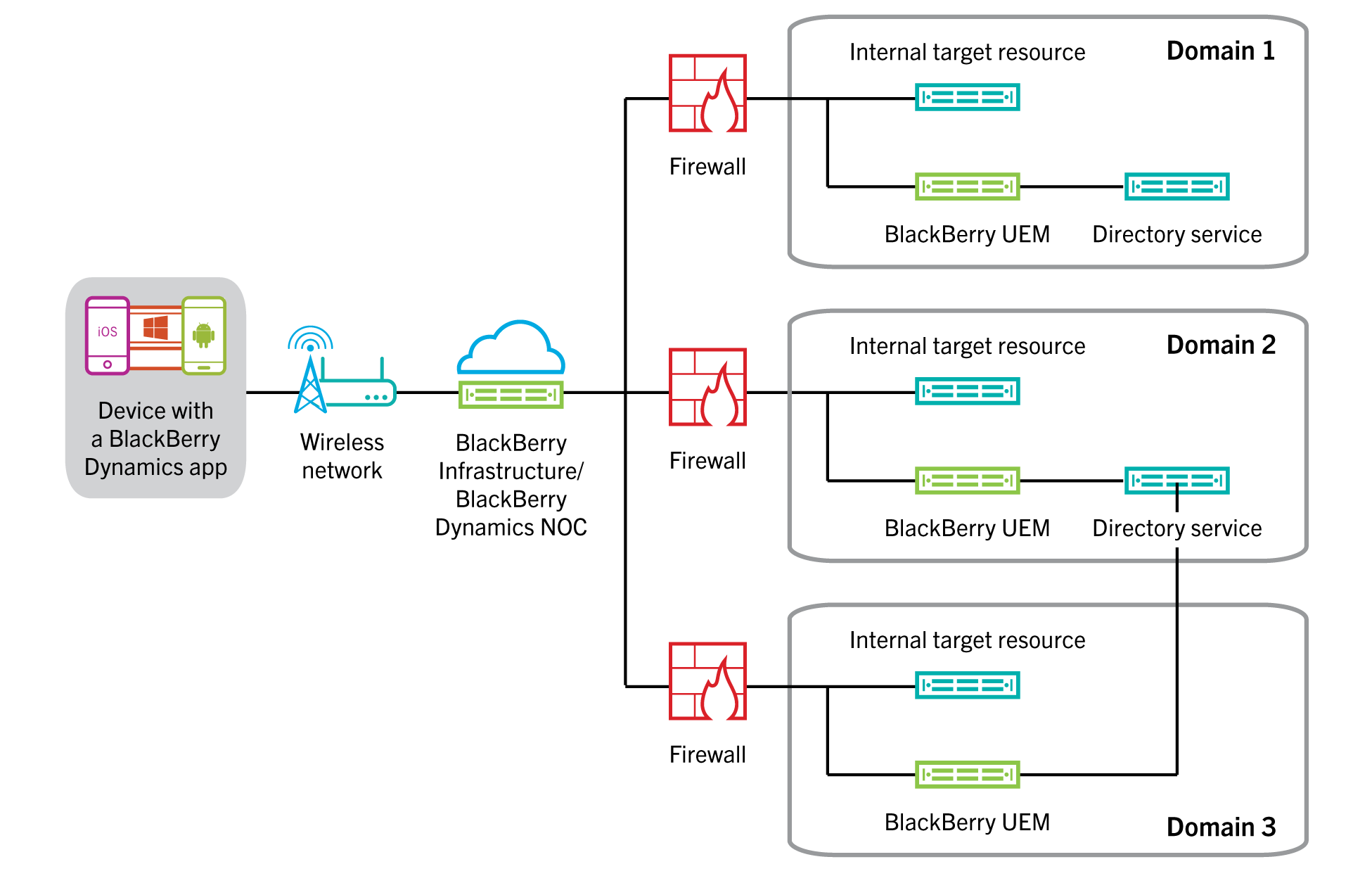
In a multi-realm KCD environment, the
BlackBerry
Dynamics
client selects a BlackBerry UEM Core
to process the KCD request based upon the DNS domain of the target server. Once the target is determined to be a KCD target, the BlackBerry
Dynamics
client determines the list of BlackBerry UEM Core
servers that are within the same DNS domain as the target, then randomly selects from this list (based on priorities) a BlackBerry UEM Core
to process the request.If there is no such DNS match (no
BlackBerry UEM Core
servers are within the same DNS domain as the target), the client randomly selects from the list of all BlackBerry UEM Core
servers.When a resource (for example,
For more information, visit support.blackberry.com/community to read article 49304.
Microsoft
Exchange
) has an FQDN name that doesn’t accurately reflect the Kerberos
realm the resource is in, then BlackBerry UEM
may not be able to properly authenticate the resource. For example, if the resource has a DNS pool name of cas.domain.com but the actual servers behind that DNS pool name are server1.alternatedomain.domain.com and server2.alternatedomain.domain.com, then the SDK will not be able to find a BlackBerry UEM Core
server within the correct realm.
The SDK compares the target host DNS domain to the DNS domain of all the
BlackBerry UEM Core
servers so that the comparison can be done offline on the device as soon as the Kerberos request occurs, with no additional fetches. If the list of Core servers in the same DNS domain as the target is empty, the SDK returns the full list of servers. Otherwise, it uses the previously generated list. The list is then randomised and further sorted to ensure this also meets the priority as well (the primaries first). The SDK selects the top two entries and initiates the KCD request to the top-listed Core server. If that request fails, the SDK sends the request to the second Core server.