Data flow: BBM Enterprise key exchange process
BBM Enterprise
key exchange process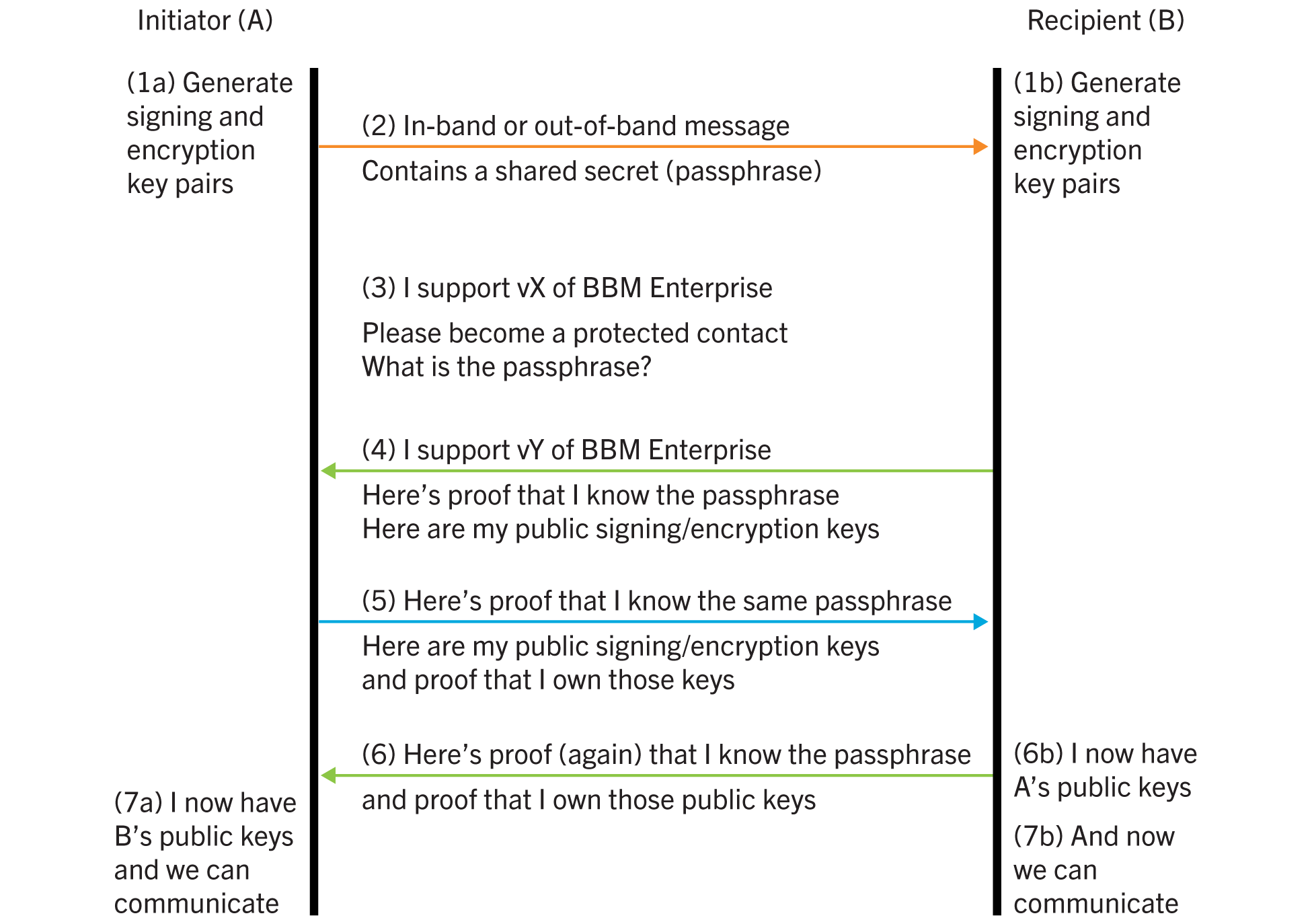
The
BBM Enterprise
key exchange uses the following steps:
- Each device performs the following actions:
- Generates a long-lived encryption key pair
- Generates a long-lived signing key pair
- The shared secret passphrase is exchanged using an automatic or manual passphrase exchange method.
- The initiator sends the firstBBM Enterprisemessage, which is an invitation that contains the initiator's contact information and the highest version (vX) ofBBM Enterprisethat they support.
- The recipient responds to the invitation and provides:
- The highest version (vY) ofBBM Enterprisethat the recipient supports
- Proof that they know the passphrase
- The recipient's long-lived public encryption and signing keys
- The initiator responds to the acceptance and provides:
- Proof that the initiator knows the passphrase
- The initiator's long-lived public encryption and signing keys
- Proof that the initiator has the private keys that correspond to the public keys that they claim to own
- The recipient responds with proof the recipient owns the private keys.
- After the initiator verifies the final message from the recipient, each party knows the other’s public keys and that they belong to someone who knows both the associated private keys and the passphrase. (Assuming that only the recipient and the initiator know the passphrase, they can confirm that the public keys belong to each other.)
- If an in-band shared secret is exchanged, once initial keys have been exchanged between twoBBM Enterprisecontacts, subsequent key exchanges will result in notification to a user when their remote contact has exchanged keys again.