Data flow: Creating a BBM Enterprise conference
BBM Enterprise
conference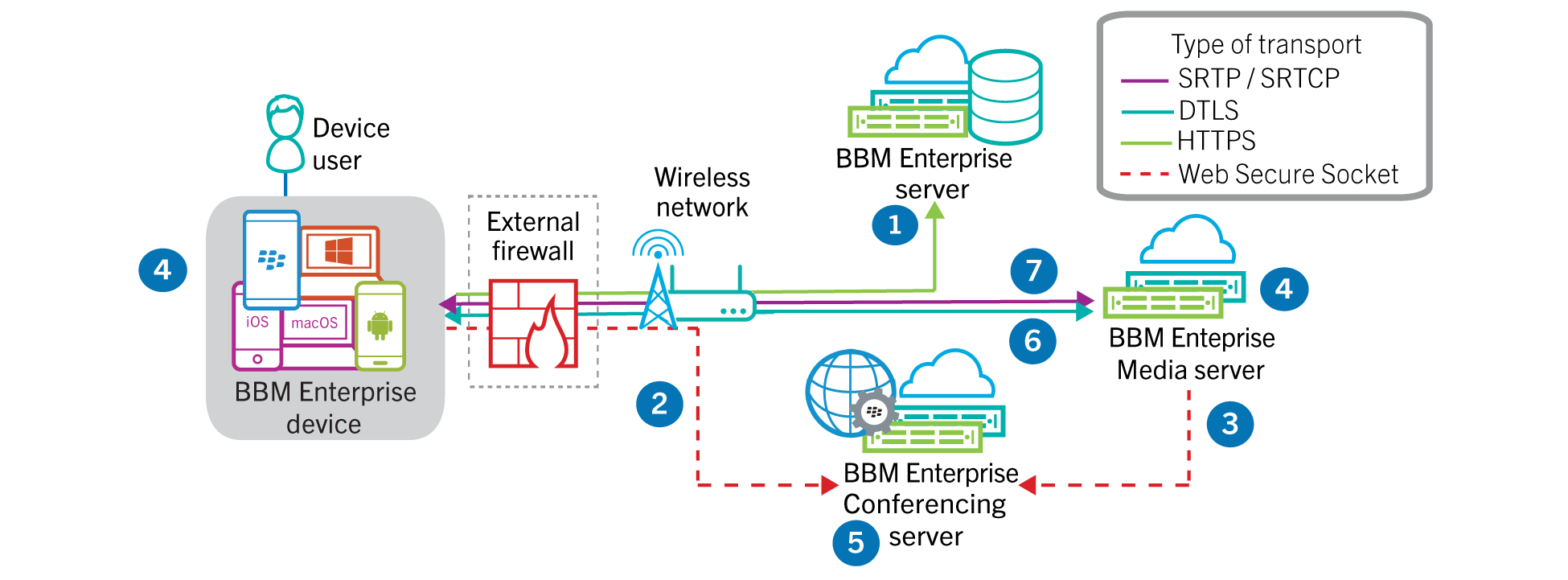
- A BBM Enterprise that wants to host or join a conference is authorized with a secure, short-lived permission grant issued by the BBM Enterprise server, following validation of the user against their organization’s policies.
- The BBM Enterprise user connects to the BBM Enterprise Conferencing server and is authenticated using the issued permission grant.
- The BBM Enterprise Conferencing server initiates a conference hosting/joining flow with the BBM Enterprise media server over a secure, authenticated connection within the BlackBerry Infrastructure.
- The BBM Enterprise app and media server generate a self-signed certificate for establishing the DTLS connection in accordance with RFC5763 of DTLS-SRTP.
- The BBM Enterprise app and media server exchange DTLS fingerprints via an SDP payload using a WSS (Web Secure Sockets) connection to the BBM Enterprise Conferencing server. Exchanging DTLS fingerprints over a trusted proxy provides assurance that the eventual DTLS connection between BBM Enterprise app and the media server has not been subject to MITM attack.
- The BBM Enterprise app and the media server negotiate SRTP encryption keys for real-time communication over the established DTLS connection in accordance with RFC5764 specification of DTLS-SRTP and RFC3711 of SRTP.
- Encryption: AES-128 CTR/CM or AES-128 in GCM as per RFC3711.
- Message Authentication and Integrity: HMAC-SHA1-80 as per RFC3711.
- KDF: DTLS PRF and SRTP AES-CM KDF as per RFC5
- Encrypted real-time media flows directly between the BBM Enterprise app and the media server.>