You can use the management console to evaluate the risk level of a file. This feature gives you insight into how the CylancePROTECT Desktop agent would classify a file that it identifies on a device.
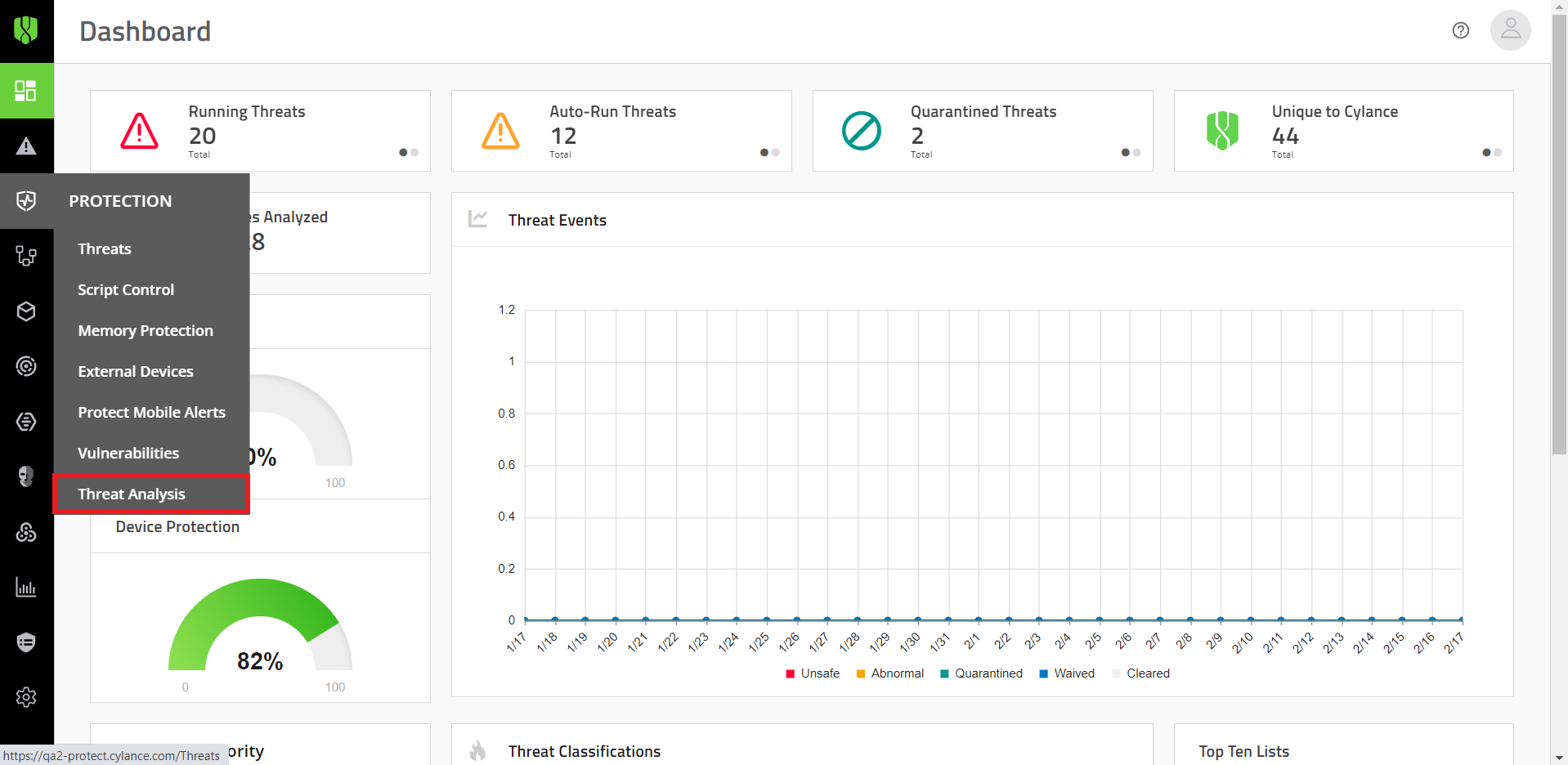
1. Click Protection > Threat Analysis
2. Do one of the following:
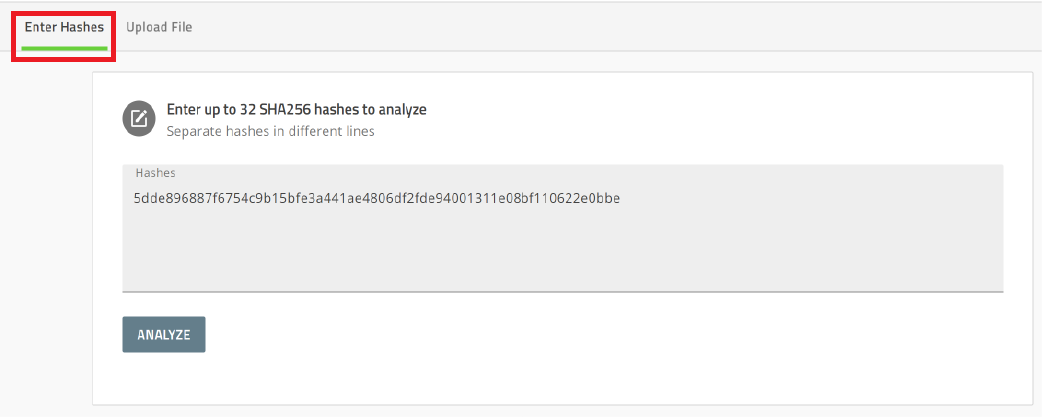
To identify the file by hash, in the Hashes field, type or paste SHA256 hashes
Add each hash on a new line.
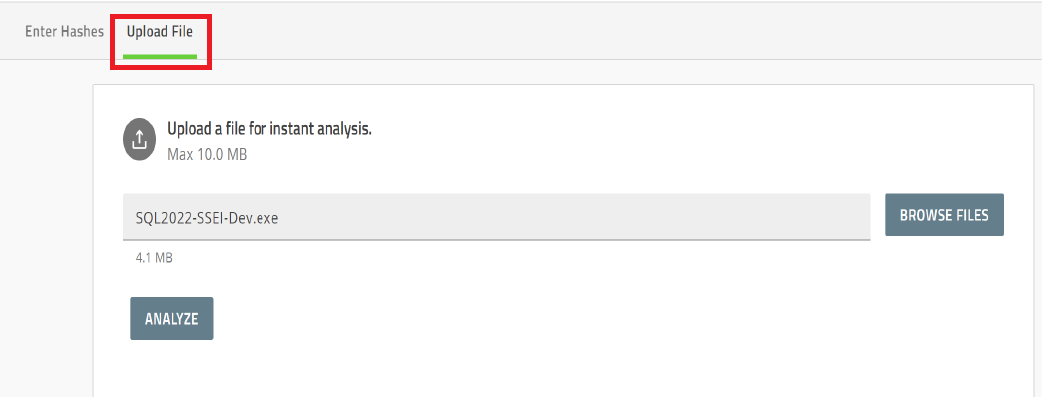
To upload the file, on the Upload File tab, click Browse Files
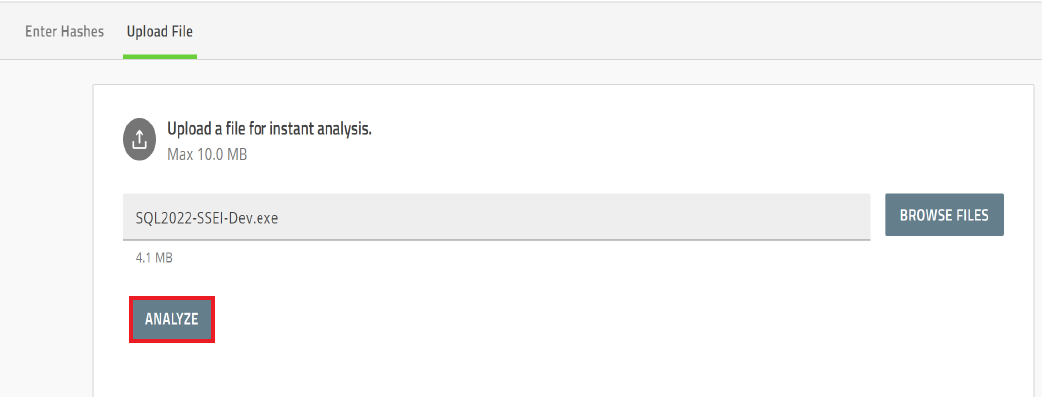
3. Click Analyze
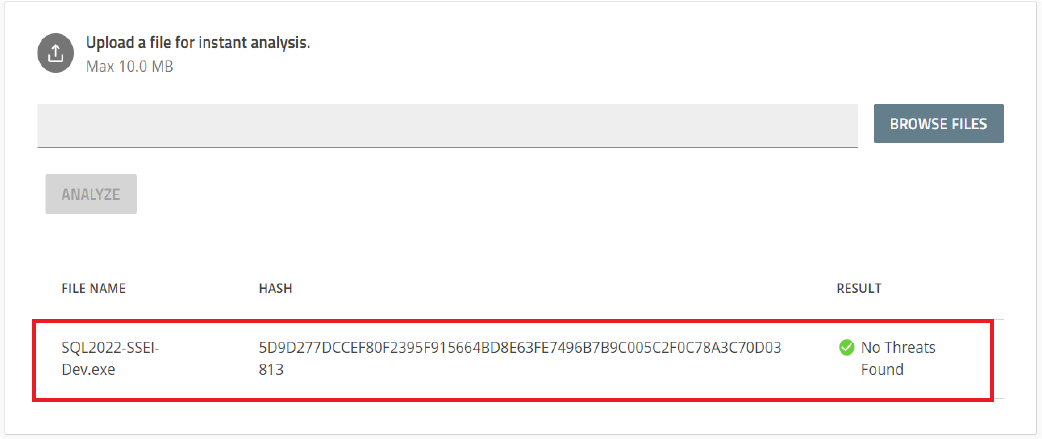
4. Check the result
To learn more about the Cylance Endpoint Security management console and file risk analysis, see the Cylance Endpoint Security Administration Guide.