Four simple steps to configure your OneLogin (SAML) authenticator to provide administrators with SSO access to the Cylance console.
Authenticators that were created before December 2023 do not allow users to directly access the Cylance console from their IDP console. To allow users to access the Cylance console from your IDP, you must generate a new SSO callback URL. This URL is generated when a new authenticator is created.
Important: Complete these steps only if your authenticator was created before December 2023 and you want to enable the IDP-initiated Proxy feature to allow users to use single sign-on (SSO) to access the Cylance console after logging in to the users’ OneLogin portal.
Before you begin: Verify if your OneLogin and Cylance Endpoint Security is enabled for SSO access to the management console. Complete the following steps:
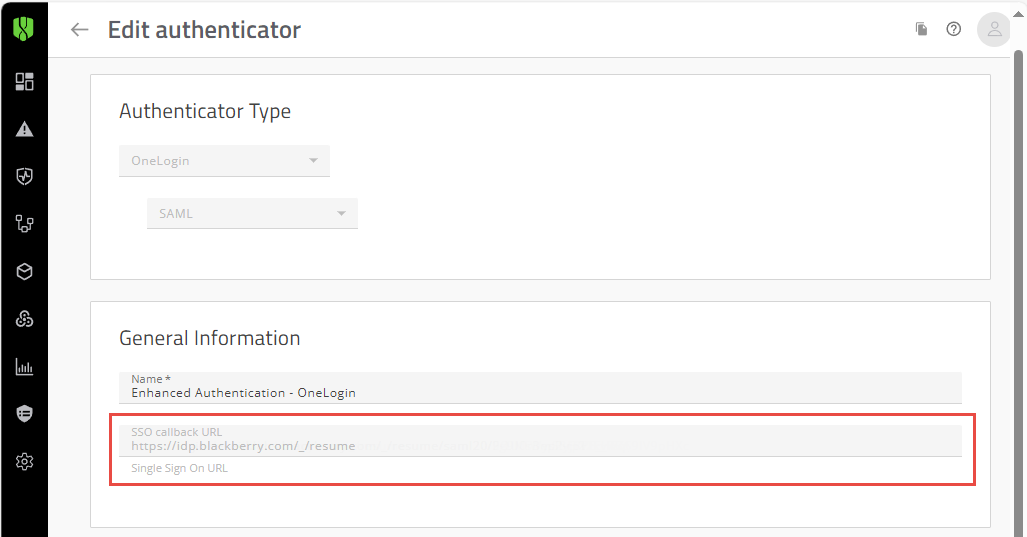
In the Cylance console, open the OneLogin SAML authenticator (Settings > Authentication).
• If the SSO callback URL is in the format of https://login.eid.blackberry.com/_/resume/saml20/<hash>, no further action is required.
• If the SSO callback URL is “https://idp.blackberry.com/_/resume”, complete the steps in this workflow to enable the IDP-initiated Proxy feature.
In this workflow, you will complete the following tasks:
- In the Cylance console, you will
a. Generate a new SSO Callback URL.
b. Update your authentication policy. - In the OneLogin environment, update the ACS (Consumer) URL Validator, the ACS (Consumer) URL, and Single Logout URL with the SSO callback URL that was generated in the Cylance console.
Important: The claim names in the OneLogin configuration and the Cylance Endpoint Security authenticator configuration must match the claim names to allow the management console to retrieve the users’ credentials. If they do not match, users cannot sign in to the management console.
The following table lists the settings that you will record from the Cylance console and update in the OneLogin console.
Cylance Console authenticator |
OneLogin console |
| SSO Callback URL The updated URL will be in the format of https://login.eid.blackberry.com/_/resume/saml20/<hash>. |
• ACS (Consumer) URL Validator* • ACS (Consumer) URL* • Single Logout URL |
The following tasks will walk you through the steps to update your SSO callback URL and enable the IDP-initiated Proxy feature.
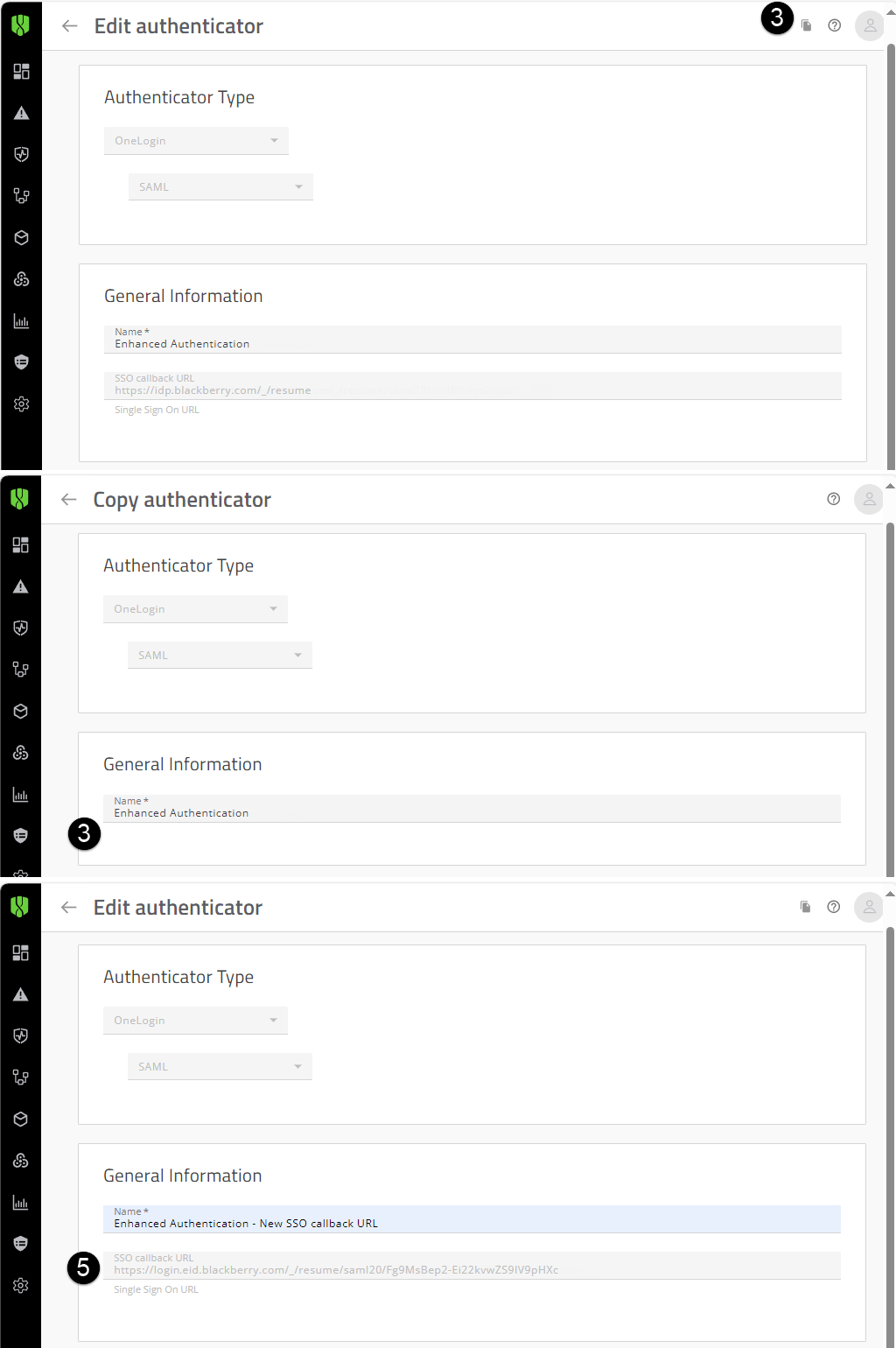
1. In the Cylance console, generate a new SSO Callback URL.
Use the copy option to copy your authenticator information and create the new SSO callback URL.
In the image, the numbers correspond to the step number in the procedure; not all steps are represented in the image.
- Open the Authenticators screen (Settings > Authentication).
- Click the current OneLogin SAML authenticator (for example, Enhanced Authentication).
- Click the Copy icon in the upper-right hand corner of the screen (See image to the left).
When you click copy, the existing Authenticator heading changes from “Edit authenticator” to “Copy authenticator” and the current SSO callback URL is removed (see image to the left). - Update the name of the copied authenticator (for example, Enhanced Authentication – New SSO callback URL). Click Save.
- Open the updated authenticator. Record the SSO callback URL (see image to the left).
Verify that the SSO URL is in the format of https://login.eid.blackberry.com/_/resume/saml20/<hash>. This URL will be added to the OneLogin console, ACS (Consumer) URL Validator field, the ACS (Consumer) URL field, and the Single Logout URL field in a later step.
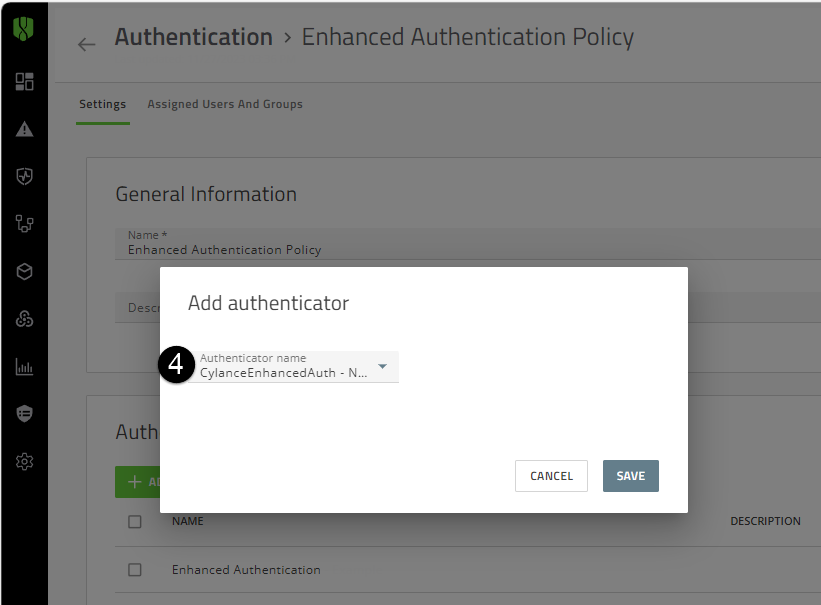
2. Update the Authentication policy with the new SSO callback URL.
Add the updated authenticator to your authentication policy. You can also add the updated authenticator to the default authentication policies for the console, CylancePROTECT Mobile app, or CylanceGATEWAY agent.
Assign the policy to one administrator to verify the sign-in policy is functioning as expected. Only one policy type can be assigned to a user. You can then assign the authentication policy to your users.
- In the image, the numbers correspond to the step number in the procedure; not all steps are represented in the image.
- On the menu bar, click Settings > User Policy.
- Click the Authentication tab.
- Click the authentication policy that you created for your users.
- In the Authenticator rules section, click Add Authenticator. In the Add authenticator dialog box, select the copied authenticator (Enhanced Authentication – New SSO callback URL) that was created in step 1 (see image to the left).
- Click Save.
- Delete the current SAML authenticator from the Authentication rules list.
- Click Save.
- Delete the original OneLogin authenticator (for example, Enhanced Authentication).
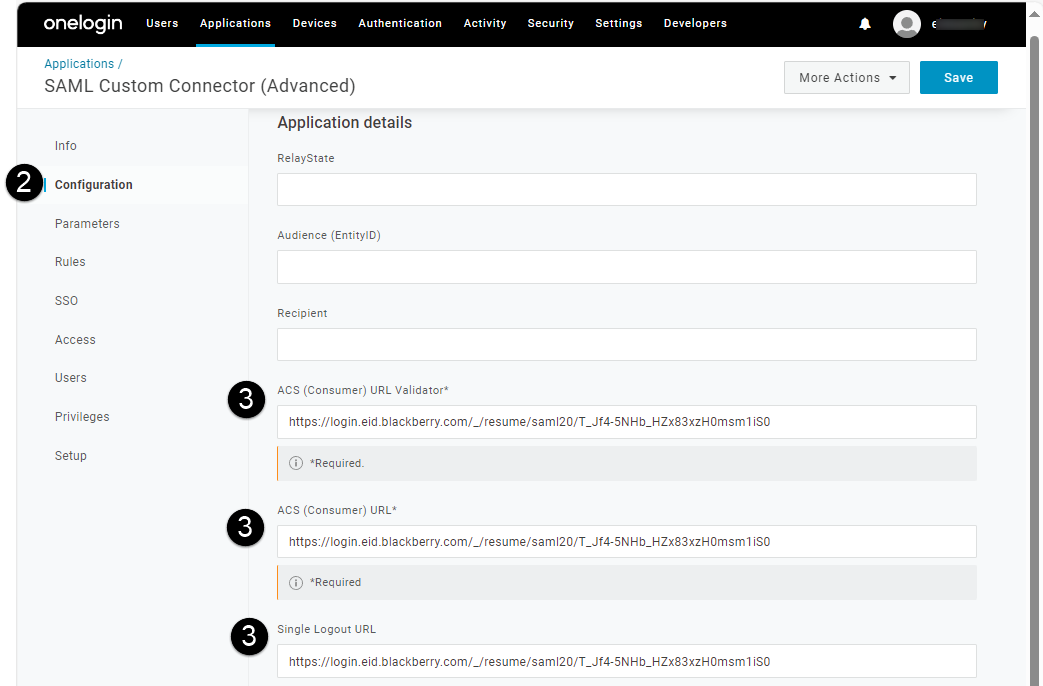
3. In the OneLogin console, update the required configuration URLs in the SAML Custom Connector (Advanced), Configuration screen.
Replace the current URL in the ACS (Consumer) URL Validator, the ACS (Consumer) URL, and Single Logout URL fields with the newly generated SSO callback URL to allow OneLogin users to communicate with and access the Cylance console directly from the OneLogin users’ portal.
- Open the current SAML application (Applications > Applications).
- On the left menu bar, click Configuration (see image to the left).
- In the following fields, delete the current URL and paste the SSO callback URL that you recorded in step 1 (see image to the left). Verify that the SSO URL is in the format of https://login.eid.blackberry.com/_/resume/saml20/<hash>.
• ACS (Consumer) URL Validator*
• ACS (Consume) URL*
• Single Logout URL
- Click Save.
- Assign users or groups to an application. When users or groups are assigned to an application, it will appear in the users’ OneLogin user portal and allow the users to directly access the Cylance console using the assigned application. For more information on how to assign an application, see your OneLogin documentation.
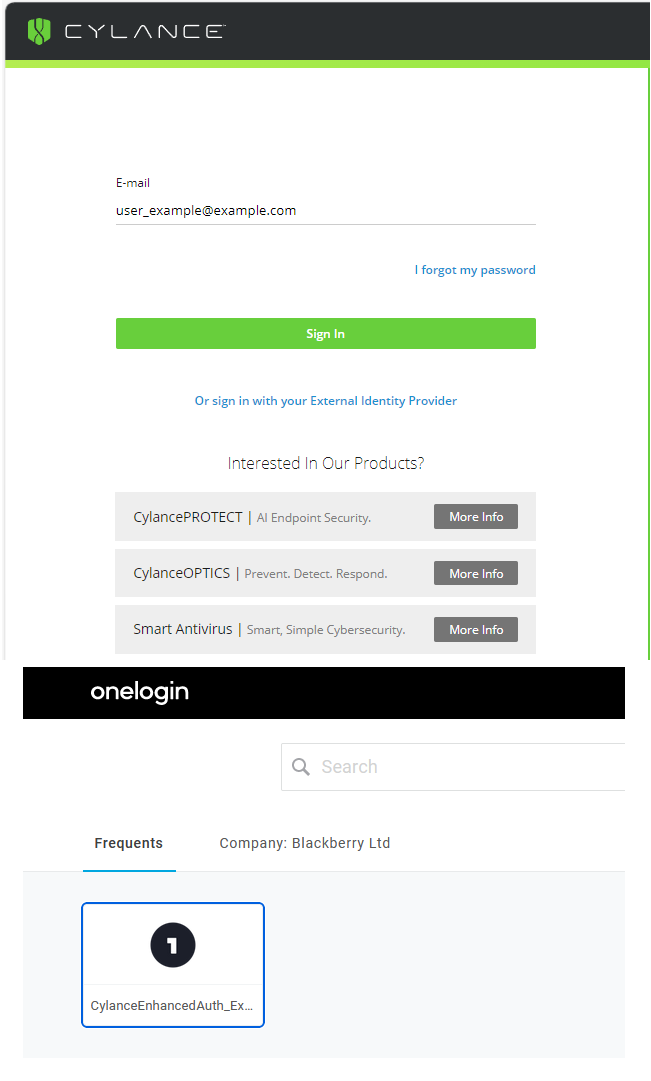
4. Verify that you can sign-in to the Cylance console.
- Verify that you can sign out and sign in to the Cylance console from the sign-in page using the administrator account with the updated authentication policy that was applied in step 2 and your OneLogin credentials.
Warning: Make sure that you sign in to the Cylance console from the primary sign-in page using your OneLogin credentials. If you test the sign in from the “Or sign in with your External Identity Provider” page and then Disable Custom Authentication, you may become locked out of the console.|
- Verify that you can sign in using the application that you were assigned in step 3. If you cannot access the console from the application, visit support.blackberry.com/community to read article 114834.

5. Step 5 action
You have successfully enabled the IDP-initiated Proxy feature.
Users can now sign-in to the Cylance console using one of the following methods:
• Cylance console sign in: Go to the Cylance Console Sign-in page and sign in directly using your OneLogin authentication (see the image to the left).
• IDP-initiated sign in: Sign in to your user’s portal and click the application that was assigned in step 3 to Single Sign-in to the Cylance console (see the image to the left).